#AI data breach
Explore tagged Tumblr posts
Text
DeepSeek, Compromis de o Breșă Majoră de Securitate: Peste un Milion de Conversații Expuse Online
🚨 Un nou scandal de securitate zguduie lumea AI: DeepSeek, startup-ul chinez care a provocat neliniște pe burse la începutul săptămânii, a fost prins într-un incident grav de securitate. O bază de date neprotejată a fost descoperită expusă online, permițând accesul neautorizat la peste un milion de conversații private între utilizatori și chatbot-ul său, alături de informații tehnice…
#AI chatbot#AI data breach#AI vulnerability#API security#atac cibernetic#bam#breșă de date#chei API#ClickHouse#Conversații private#cyber threat#cybersecurity#cybersecurity incident#data privacy#database exposure#date confidențiale#DeepSeek#diagnoza#exposed data#expunere date#hacking#hacking risk#neamt#roman#securitate cibernetică#security breach#user privacy#vulnerabilitate AI#Wiz Research
0 notes
Text
"Just weeks before the implosion of AllHere, an education technology company that had been showered with cash from venture capitalists and featured in glowing profiles by the business press, America’s second-largest school district was warned about problems with AllHere’s product.
As the eight-year-old startup rolled out Los Angeles Unified School District’s flashy new AI-driven chatbot — an animated sun named “Ed” that AllHere was hired to build for $6 million — a former company executive was sending emails to the district and others that Ed’s workings violated bedrock student data privacy principles.
Those emails were sent shortly before The 74 first reported last week that AllHere, with $12 million in investor capital, was in serious straits. A June 14 statement on the company’s website revealed a majority of its employees had been furloughed due to its “current financial position.” Company founder and CEO Joanna Smith-Griffin, a spokesperson for the Los Angeles district said, was no longer on the job.
Smith-Griffin and L.A. Superintendent Alberto Carvalho went on the road together this spring to unveil Ed at a series of high-profile ed tech conferences, with the schools chief dubbing it the nation’s first “personal assistant” for students and leaning hard into LAUSD’s place in the K-12 AI vanguard. He called Ed’s ability to know students “unprecedented in American public education” at the ASU+GSV conference in April.
Through an algorithm that analyzes troves of student information from multiple sources, the chatbot was designed to offer tailored responses to questions like “what grade does my child have in math?” The tool relies on vast amounts of students’ data, including their academic performance and special education accommodations, to function.
Meanwhile, Chris Whiteley, a former senior director of software engineering at AllHere who was laid off in April, had become a whistleblower. He told district officials, its independent inspector general’s office and state education officials that the tool processed student records in ways that likely ran afoul of L.A. Unified’s own data privacy rules and put sensitive information at risk of getting hacked. None of the agencies ever responded, Whiteley told The 74.
...
In order to provide individualized prompts on details like student attendance and demographics, the tool connects to several data sources, according to the contract, including Welligent, an online tool used to track students’ special education services. The document notes that Ed also interfaces with the Whole Child Integrated Data stored on Snowflake, a cloud storage company. Launched in 2019, the Whole Child platform serves as a central repository for LAUSD student data designed to streamline data analysis to help educators monitor students’ progress and personalize instruction.
Whiteley told officials the app included students’ personally identifiable information in all chatbot prompts, even in those where the data weren’t relevant. Prompts containing students’ personal information were also shared with other third-party companies unnecessarily, Whiteley alleges, and were processed on offshore servers. Seven out of eight Ed chatbot requests, he said, are sent to places like Japan, Sweden, the United Kingdom, France, Switzerland, Australia and Canada.
Taken together, he argued the company’s practices ran afoul of data minimization principles, a standard cybersecurity practice that maintains that apps should collect and process the least amount of personal information necessary to accomplish a specific task. Playing fast and loose with the data, he said, unnecessarily exposed students’ information to potential cyberattacks and data breaches and, in cases where the data were processed overseas, could subject it to foreign governments’ data access and surveillance rules.
Chatbot source code that Whiteley shared with The 74 outlines how prompts are processed on foreign servers by a Microsoft AI service that integrates with ChatGPT. The LAUSD chatbot is directed to serve as a “friendly, concise customer support agent” that replies “using simple language a third grader could understand.” When querying the simple prompt “Hello,” the chatbot provided the student’s grades, progress toward graduation and other personal information.
AllHere’s critical flaw, Whiteley said, is that senior executives “didn’t understand how to protect data.”
...
Earlier in the month, a second threat actor known as Satanic Cloud claimed it had access to tens of thousands of L.A. students’ sensitive information and had posted it for sale on Breach Forums for $1,000. In 2022, the district was victim to a massive ransomware attack that exposed reams of sensitive data, including thousands of students’ psychological evaluations, to the dark web.
With AllHere’s fate uncertain, Whiteley blasted the company’s leadership and protocols.
“Personally identifiable information should be considered acid in a company and you should only touch it if you have to because acid is dangerous,” he told The 74. “The errors that were made were so egregious around PII, you should not be in education if you don’t think PII is acid.”
Read the full article here:
https://www.the74million.org/article/whistleblower-l-a-schools-chatbot-misused-student-data-as-tech-co-crumbled/
17 notes
·
View notes
Text
Are AI-Powered Traffic Cameras Watching You Drive?
New Post has been published on https://thedigitalinsider.com/are-ai-powered-traffic-cameras-watching-you-drive/
Are AI-Powered Traffic Cameras Watching You Drive?


Artificial intelligence (AI) is everywhere today. While that’s an exciting prospect to some, it’s an uncomfortable thought for others. Applications like AI-powered traffic cameras are particularly controversial. As their name suggests, they analyze footage of vehicles on the road with machine vision.
They’re typically a law enforcement measure — police may use them to catch distracted drivers or other violations, like a car with no passengers using a carpool lane. However, they can also simply monitor traffic patterns to inform broader smart city operations. In all cases, though, they raise possibilities and questions about ethics in equal measure.
How Common Are AI Traffic Cameras Today?
While the idea of an AI-powered traffic camera is still relatively new, they’re already in use in several places. Nearly half of U.K. police forces have implemented them to enforce seatbelt and texting-while-driving regulations. U.S. law enforcement is starting to follow suit, with North Carolina catching nine times as many phone violations after installing AI cameras.
Fixed cameras aren’t the only use case in action today, either. Some transportation departments have begun experimenting with machine vision systems inside public vehicles like buses. At least four cities in the U.S. have implemented such a solution to detect cars illegally parked in bus lanes.
With so many local governments using this technology, it’s safe to say it will likely grow in the future. Machine learning will become increasingly reliable over time, and early tests could lead to further adoption if they show meaningful improvements.
Rising smart city investments could also drive further expansion. Governments across the globe are betting hard on this technology. China aims to build 500 smart cities, and India plans to test these technologies in at least 100 cities. As that happens, more drivers may encounter AI cameras on their daily commutes.
Benefits of Using AI in Traffic Cameras
AI traffic cameras are growing for a reason. The innovation offers a few critical advantages for public agencies and private citizens.
Safety Improvements
The most obvious upside to these cameras is they can make roads safer. Distracted driving is dangerous — it led to the deaths of 3,308 people in 2022 alone — but it’s hard to catch. Algorithms can recognize drivers on their phones more easily than highway patrol officers can, helping enforce laws prohibiting these reckless behaviors.
Early signs are promising. The U.K. and U.S. police forces that have started using such cameras have seen massive upticks in tickets given to distracted drivers or those not wearing seatbelts. As law enforcement cracks down on such actions, it’ll incentivize people to drive safer to avoid the penalties.
AI can also work faster than other methods, like red light cameras. Because it automates the analysis and ticketing process, it avoids lengthy manual workflows. As a result, the penalty arrives soon after the violation, which makes it a more effective deterrent than a delayed reaction. Automation also means areas with smaller police forces can still enjoy such benefits.
Streamlined Traffic
AI-powered traffic cameras can minimize congestion on busy roads. The areas using them to catch illegally parked cars are a prime example. Enforcing bus lane regulations ensures public vehicles can stop where they should, avoiding delays or disruptions to traffic in other lanes.
Automating tickets for seatbelt and distracted driving violations has a similar effect. Pulling someone over can disrupt other cars on the road, especially in a busy area. By taking a picture of license plates and sending the driver a bill instead, police departments can ensure safer streets without adding to the chaos of everyday traffic.
Non-law-enforcement cameras could take this advantage further. Machine vision systems throughout a city could recognize congestion and update map services accordingly, rerouting people around busy areas to prevent lengthy delays. Considering how the average U.S. driver spent 42 hours in traffic in 2023, any such improvement is a welcome change.
Downsides of AI Traffic Monitoring
While the benefits of AI traffic cameras are worth noting, they’re not a perfect solution. The technology also carries some substantial potential downsides.
False Positives and Errors
The correctness of AI may raise some concerns. While it tends to be more accurate than people in repetitive, data-heavy tasks, it can still make mistakes. Consequently, removing human oversight from the equation could lead to innocent people receiving fines.
A software bug could cause machine vision algorithms to misidentify images. Cybercriminals could make such instances more likely through data poisoning attacks. While people could likely dispute their tickets and clear their name, it would take a long, difficult process to do so, counteracting some of the technology’s efficiency benefits.
False positives are a related concern. Algorithms can produce high false positive rates, leading to more charges against innocent people, which carries racial implications in many contexts. Because data biases can remain hidden until it’s too late, AI in government applications can exacerbate problems with racial or gender discrimination in the legal system.
Privacy Issues
The biggest controversy around AI-powered traffic cameras is a familiar one — privacy. As more cities install these systems, they record pictures of a larger number of drivers. So much data in one place raises big questions about surveillance and the security of sensitive details like license plate numbers and drivers’ faces.
Many AI camera solutions don’t save images unless they determine it’s an instance of a violation. Even so, their operation would mean the solutions could store hundreds — if not thousands — of images of people on the road. Concerns about government surveillance aside, all that information is a tempting target for cybercriminals.
U.S. government agencies suffered 32,211 cybersecurity incidents in 2023 alone. Cybercriminals are already targeting public organizations and critical infrastructure, so it’s understandable why some people may be concerned that such groups would gather even more data on citizens. A data breach in a single AI camera system could affect many who wouldn’t have otherwise consented to giving away their data.
What the Future Could Hold
Given the controversy, it may take a while for automated traffic cameras to become a global standard. Stories of false positives and concerns over cybersecurity issues may delay some projects. Ultimately, though, that’s a good thing — attention to these challenges will lead to necessary development and regulation to ensure the rollout does more good than harm.
Strict data access policies and cybersecurity monitoring will be crucial to justify widespread adoption. Similarly, government organizations using these tools should verify the development of their machine-learning models to check for and prevent problems like bias. Regulations like the recent EU Artificial Intelligence Act have already provided a legislative precedent for such qualifications.
AI Traffic Cameras Bring Both Promise and Controversy
AI-powered traffic cameras may still be new, but they deserve attention. Both the promises and pitfalls of the technology need greater attention as more governments seek to implement them. Higher awareness of the possibilities and challenges surrounding this innovation can foster safer development for a secure and efficient road network in the future.
#2022#2023#adoption#ai#AI-powered#Algorithms#Analysis#applications#artificial#Artificial Intelligence#attention#automation#awareness#betting#Bias#biases#breach#bug#Cameras#Cars#change#chaos#China#cities#critical infrastructure#cybercriminals#cybersecurity#data#data breach#data poisoning
5 notes
·
View notes
Text
Bad news: Tumblr will be partnering with OpenAI and Midjourney
(You may have to 'subscribe' to read the whole article, but it's free, and I highly recommend that you do read the whole thing)
Decent-ish news: supposedly, we'll be able to opt out (if there is an option, I recommend double checking that it's still selected every once in a while
Bad news: Tumblr 'accidentally' gave all sorts of data to OpenAI/Midjourney that it shouldn't have 😑
FFS, tech bros, just leave us alone
#tech#technology#ai art is theft#AI#artificial intelligence#Midjourney#open AI#tumblr#data breach#opt out#FFS just leave us alone#read#article#news#404 Media
9 notes
·
View notes
Text
youtube
#Aperture#video essay#algorithm#algorithms#Eric Loomis#COMPAS#thought piece#computer#computer program#data#data brokers#targeted ads#data breach#terminal#the silver machine#AI#machine learning#healthcare#tech#technology#profit#Youtube
2 notes
·
View notes
Text
#sorry maybe a hot take but if you are gonna have a fit everytime someone uses a huge umbrella term that has been used for decades thats on u#like its not... deliberate? its just happening because AI is literally a word people use to mean#'a more complex algorithm that can make decisions on its own based on parameters and context someone programmed in'#there isnt some huge magical difference between how the photoshop fix tool works and how midjourney works#one of them is just WAY more complex (and happens to be WAY more unethical data-rights-wise) but at it's core its actually the same thing#the thing on your phone keyboard that suggests which word to use next based on what words u usually use next#and chatGPT are also very similar in how they work its just that one is bigger and more unethical and uses more water than a small country#like. its not that there is some conspiracy going on to make the 'new AI' seem like the 'old AI'. its the same stuff but more advanced.#chatbots that can hold really complex dialogue arent *all* that different from a well-written video game NPC AI#and you have to look into context if someone says 'this game uses AI' because AI literally IS a huge umbrella term#like. its like being mad when someone says their website has an algorithm just bc you#immediately assume its the bad evil tiktok algorithm everyone talks about and dont realize 'algorithm' is just short of saying#'there's code on my website' you knowwww. there ISNT a meaningful difference between these AIs except that some are sourced unethically#and this person just confidently says things that are completely wrong and lack any critical thought or nuance (tags from @zevranunderstander)




#huge unethical data breaches are a problem that is neither emblematic of nor exclusive to ai#also the algorithm thing. i cannot stress enough how much algorithm is a neutral word. my god
47K notes
·
View notes
Text
Use this guide to the newest trends and best practices to safeguard your company from new cyberthreats in 2025.
#cybersecurity#Cybersecurity#Cyber Security Trends#2025#Zero Trust#Cloud Security#AI#Artificial Intelligence#Data Protection#IoT Security#Ransomware#Phishing#Data Breach#Biometric Authentication#Blockchain#Cyber Resilience#Deepfakes#5G Security
0 notes
Text
#Tags:Advanced Persistent Threats (APTs)#AI in Cybersecurity#Cloud Security#Cyber Defense Strategies#Cyber Threat Trends 2025#Cybersecurity#Data Breaches#Digital Resilience#facts#Incident Response#IoT Security#life#Malware#Podcast#Ransomware#Ransomware-as-a-Service#serious#straight forward#Threat Intelligence#truth#upfront#website#Worms
1 note
·
View note
Text
#tools#resources#data breach#haveibeenpwned#surveillance capitalism#data#privacy#data privacy#ai#social media#digital platforms#email#marketing#surveillance#advertising
0 notes
Text
I see a lot of idiots in the notes going like, "Stop fear mongering! This is only going to be an optional feature on specific high end PCs installed with this one specific snapdragon chip that can support the basic AI!"
Completely overlooking that this shouldn't be a feature on ANY computer AT ALL.
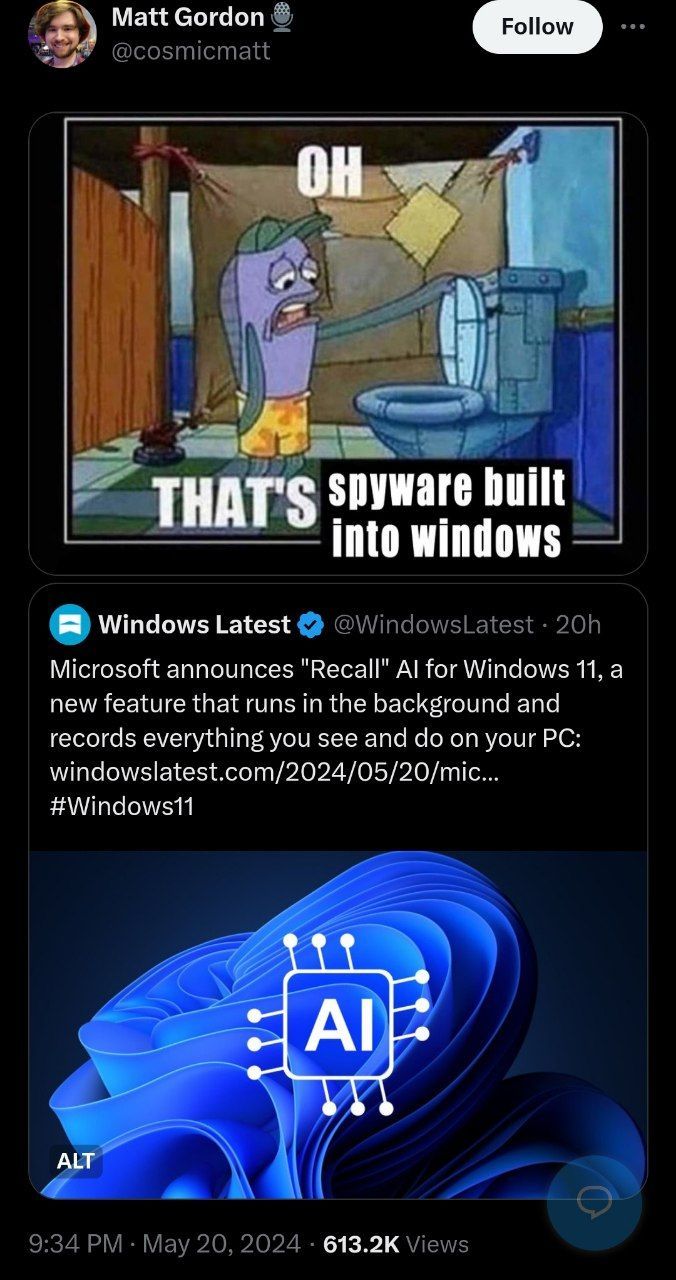
#that's a data breach waiting to happen#doesn't matter if it's optional#no one should want this#RL stuff#anti AI
102K notes
·
View notes
Text
Sitting in a meeting about how good and sophisticated and reliable AI is genuinely one of the grimmest things I ever had to sit through on god we are in dark times brother
0 notes
Text
The role of machine learning in enhancing cloud-native container security - AI News
New Post has been published on https://thedigitalinsider.com/the-role-of-machine-learning-in-enhancing-cloud-native-container-security-ai-news/
The role of machine learning in enhancing cloud-native container security - AI News


The advent of more powerful processors in the early 2000’s shipping with support in hardware for virtualisation started the computing revolution that led, in time, to what we now call the cloud. With single hardware instances able to run dozens, if not hundreds of virtual machines concurrently, businesses could offer their users multiple services and applications that would otherwise have been financially impractical, if not impossible.
But virtual machines (VMs) have several downsides. Often, an entire virtualised operating system is overkill for many applications, and although very much more malleable, scalable, and agile than a fleet of bare-metal servers, VMs still require significantly more memory and processing power, and are less agile than the next evolution of this type of technology – containers. In addition to being more easily scaled (up or down, according to demand), containerised applications consist of only the necessary parts of an application and its supporting dependencies. Therefore apps based on micro-services tend to be lighter and more easily configurable.
Virtual machines exhibit the same security issues that affect their bare-metal counterparts, and to some extent, container security issues reflect those of their component parts: a mySQL bug in a specific version of the upstream application will affect containerised versions too. With regards to VMs, bare metal installs, and containers, cybersecurity concerns and activities are very similar. But container deployments and their tooling bring specific security challenges to those charged with running apps and services, whether manually piecing together applications with choice containers, or running in production with orchestration at scale.
Container-specific security risks
Misconfiguration: Complex applications are made up of multiple containers, and misconfiguration – often only a single line in a .yaml file, can grant unnecessary privileges and increase the attack surface. For example, although it’s not trivial for an attacker to gain root access to the host machine from a container, it’s still a too-common practice to run Docker as root, with no user namespace remapping, for example.
Vulnerable container images: In 2022, Sysdig found over 1,600 images identified as malicious in Docker Hub, in addition to many containers stored in the repo with hard-coded cloud credentials, ssh keys, and NPM tokens. The process of pulling images from public registries is opaque, and the convenience of container deployment (plus pressure on developers to produce results, fast) can mean that apps can easily be constructed with inherently insecure, or even malicious components.
Orchestration layers: For larger projects, orchestration tools such as Kubernetes can increase the attack surface, usually due to misconfiguration and high levels of complexity. A 2022 survey from D2iQ found that only 42% of applications running on Kubernetes made it into production – down in part to the difficulty of administering large clusters and a steep learning curve.
According to Ari Weil at Akamai, “Kubernetes is mature, but most companies and developers don’t realise how complex […] it can be until they’re actually at scale.”
Container security with machine learning
The specific challenges of container security can be addressed using machine learning algorithms trained on observing the components of an application when it’s ‘running clean.’ By creating a baseline of normal behaviour, machine learning can identify anomalies that could indicate potential threats from unusual traffic, unauthorised changes to configuration, odd user access patterns, and unexpected system calls.
ML-based container security platforms can scan image repositories and compare each against databases of known vulnerabilities and issues. Scans can be automatically triggered and scheduled, helping prevent the addition of harmful elements during development and in production. Auto-generated audit reports can be tracked against standard benchmarks, or an organisation can set its own security standards – useful in environments where highly-sensitive data is processed.
The connectivity between specialist container security functions and orchestration software means that suspected containers can be isolated or closed immediately, insecure permissions revoked, and user access suspended. With API connections to local firewalls and VPN endpoints, entire environments or subnets can be isolated, or traffic stopped at network borders.
Final word
Machine learning can reduce the risk of data breach in containerised environments by working on several levels. Anomaly detection, asset scanning, and flagging potential misconfiguration are all possible, plus any degree of automated alerting or amelioration are relatively simple to enact.
The transformative possibilities of container-based apps can be approached without the security issues that have stopped some from exploring, developing, and running microservice-based applications. The advantages of cloud-native technologies can be won without compromising existing security standards, even in high-risk sectors.
(Image source)
#2022#agile#ai#ai news#akamai#Algorithms#anomalies#anomaly#anomaly detection#API#applications#apps#Attack surface#audit#benchmarks#breach#bug#Cloud#Cloud-Native#clusters#Companies#complexity#computing#connectivity#container#container deployment#Containers#credentials#cybersecurity#data
0 notes
Text
Fuck, that shit is stealing all your passwords isn't it? If I had an Apple I'd be looking into ripping Siri out by the roots by now, what the FUCK


FYI iPhone users!
59K notes
·
View notes
Text
Privacy Risks for Women Seeking Out-of-State Care
In this episode of Scam DamNation, host Lillian Cauldwell introduces an old type of scam still continuing in the United States targeted at women where personal information bought with a credit card tracks women who visit abortion clinics and tracks them back across state lines to their place of residence and nothing is being done about it. Senator Ron Wyden wrote an article in which he states…
#Abortion Clinics.#AI Scams.#Cell Phone#Credit Card Tracking&039;s#Data Breach#Data Brokers#Lillian Cauldwell#Privacy Risks#Scam DamNation#Scams#Senator Ron Wyden#women health#Women Rights
0 notes
Text
Mandatory Age Verification For Social Media
I had a conversation with Copilot about Mandatory Age Verification For Social Media.
The proposed Social Media Ban for under-16s by the Australian federal ALP government involves Age Verification methods that include providing ID and biometrics, such as face scanning. This approach raises significant concerns about privacy and the potential for creating a de facto Digital ID system.
Practical Implications • ID Verification: Users would need to provide some form of identification to verify their age. This could include government-issued IDs, like passports or driver's licenses.
• Biometric Data: Face scanning or other biometric methods would be used to ensure the person presenting the ID is the same person using the social media account.
• Data Collection: This process would result in the collection of sensitive personal data, including biometric information, which could be stored and potentially used for other purposes.
Concerns • Privacy: The collection and storage of biometric data and personal IDs raise significant privacy concerns. There is a risk of data breaches and misuse of this information.
• Digital ID System: While the primary goal is age verification, the requirement for biometric data and IDs effectively creates a Digital ID system for social media users.
• Accessibility: Not everyone may have access to the required forms of ID or be comfortable with biometric verification, potentially excluding some users from social media platforms.
Conclusion In practical terms, the proposed age verification methods resemble the creation of a Digital ID system.
The Digital ID Program The Digital ID Program of the Australian government is designed to be voluntary, providing a secure and convenient way for individuals to verify their identity online. However it raises concerns about the proposed Social Media Ban potentially leading to a de facto compulsory Digital ID system.
Key Points • Voluntary Nature: The current Digital ID system is voluntary, allowing individuals to choose whether or not to use it.
• Age Verification: The proposed social media ban for under-16s involves age verification methods that include providing ID and biometrics, such as face scanning.
• Potential For Compulsory Use: While the Digital ID system is voluntary, the requirement for age verification on social media platforms could effectively make it compulsory for those who wish to use these services.
Conclusion The introduction of Mandatory Age Verification For Social Media could definitely be seen as a step towards a more widespread use of Digital ID, potentially leading to concerns about privacy and the implications of a de facto compulsory system.
The Social Media Ban Is The Vaccine Passport Program Revisited Voluntary programs can evolve into mandatory requirements over time. During the Covid-19 pandemic, Vaccine Passports initially presented as voluntary measures soon became essential for accessing certain services and venues. This shift highlighted concerns about how "voluntary" programs can, in practice, become quasi-mandatory.
Parallels Between Vaccine Passports and Digital ID For Social Media • Initial Voluntariness: Both vaccine passports and the current Digital ID system started as voluntary initiatives.
• Increased Necessity: Over time, certain activities (like entering premises during the pandemic) or services (like accessing social media) required compliance with these "voluntary" measures.
• Privacy Concerns: Both programs raise significant privacy concerns, particularly regarding the collection and use of personal and biometric data.
• Public Trust: The shift from voluntary to mandatory can erode public trust and lead to resistance or backlash.
Conclusion The potential trajectory of the Social Media Ban, requiring ID and biometrics for age verification, could mirror the path of Vaccine Passports, effectively making Digital ID a necessity for certain activities.
#copilot#copillot ai#politics#social media ban#social media#vaccine passports#digital identity#digital id#privacy#data breach#biometric verification
1 note
·
View note